We are a cybersecurity service provider
On the leading edge of information security trends. We protect your business with the best available methods and technologies.
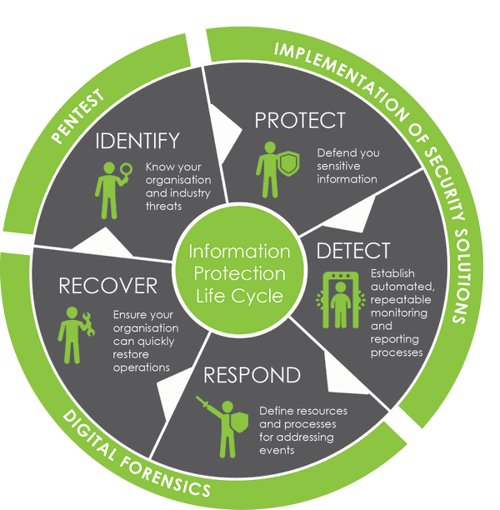
Our services are applied at all stages of your information security lifecycle. Have some special requirements? Want to know how to solve your security challenges?
We can help with
Identifying
Protection and detection
Responding and recovering
Our primary cybersecurity partners:
Is a new generation security platform. By delivering a comprehensive portfolio and empowering a growing ecosystem of partners, we are at the forefront of protecting tens of thousands of organizations across clouds, networks, and mobile devices

provides functionality for identity lifecycle management and access control. IAM includes policies, processes, and workflows for onboarding, off-boarding, identity modification, provisioning, authentication, and authorization.

Imperva products protect cloud applications, websites, web applications, critical databases, files, and Big Data repositories from hackers and insider threats, providing comprehensive data protection and controls
_transparent.png?width=200&height=113&name=RMRF_logo(%D1%86%D0%B2%D0%B5%D1%82_%D1%81%D0%BE%20%D1%81%D0%BB%D0%BE%D0%B3%D0%B0%D0%BD%D0%BE%D0%BC)_transparent.png)




